VPN Services
A VPN (virtual private network) encrypts and tunnels all Internet traffic between yourself and another computer. This computer might belong to a commercial VPN service, your organization, or a trusted contact.
Because VPN services tunnel all Internet traffic, they can be used for e-mail, instant messaging, Voice over IP (VoIP) and any other Internet service in addition to Web browsing, making everything that travels through the tunnel unreadable to anyone along the way.
If the tunnel ends outside the area where the Internet is being restricted, this can be an effective method of circumvention, since the filtering entity/server sees only encrypted data, and has no way of knowing what data is passing through the tunnel. It has the additional effect of making all your different kinds of traffic look similar to an eavesdropper.
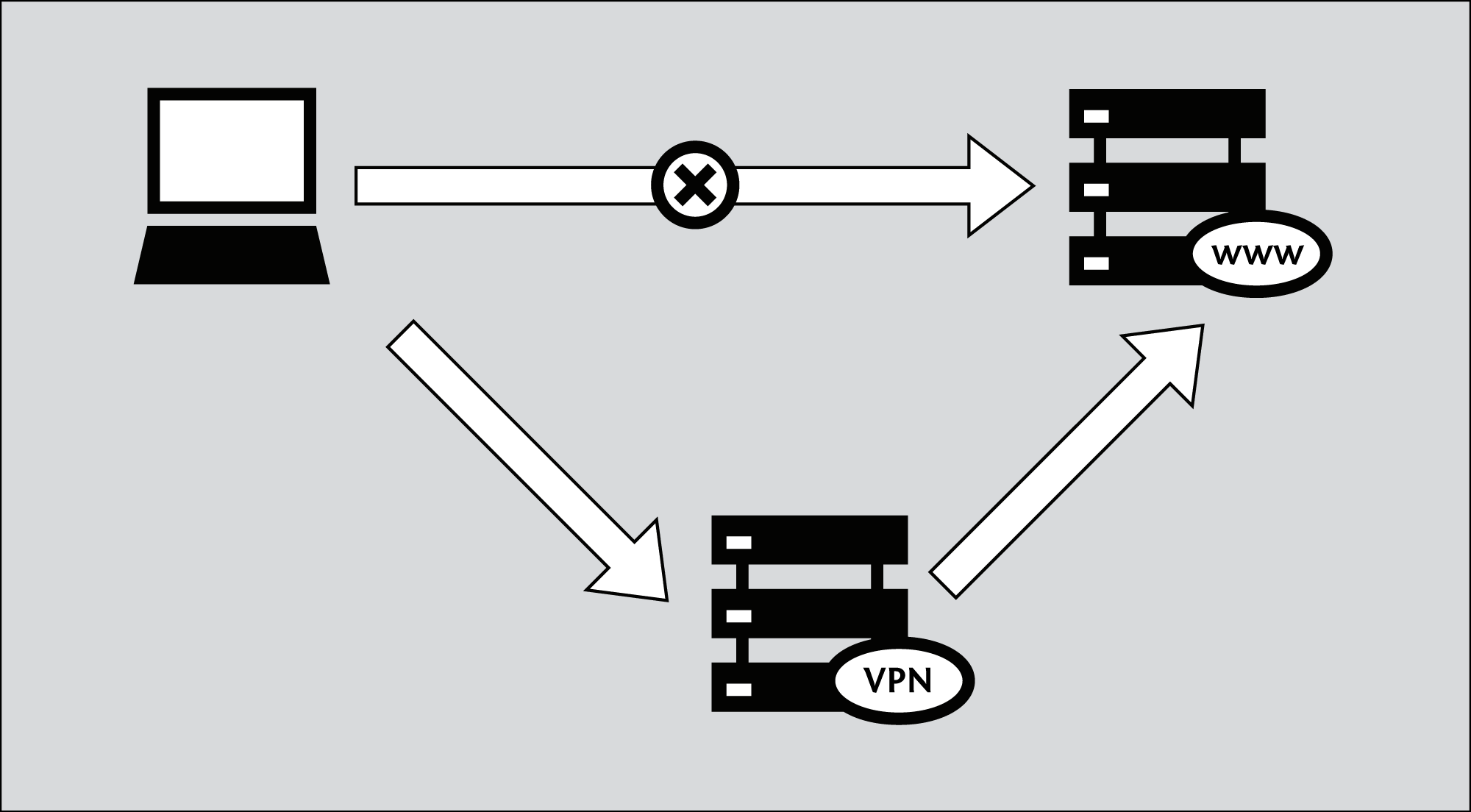
Since many international companies use VPN technology to allow employees who need access to sensitive financial or other information to access the companies' computer systems from home or other remote locations over the Internet, VPN technology is less likely to be blocked than the technologies used only for circumvention purposes.
It is important to note that the data is only encrypted as far as the end of the tunnel, and then travels unencrypted to its final destination. If, for example, you set up a tunnel to a commercial VPN provider, and then request the Web page http://news.bbc.co.uk through the tunnel, the data will be encrypted from your computer to the VPN provider's computer at the other end, but from there it will be unencrypted to the servers run by the BBC, just like normal Internet traffic. This means that the VPN provider, the BBC and anyone with control over a system between these two servers, will, in theory, be able to see what data you sent or have requested.
Using VPN services
VPN services might or might not require installation of client-side software (many rely on existing VPN support in Windows, Mac OS or GNU/Linux and so need no extra client software).
Using a VPN service requires you to trust the owners of the service, but provides a simple and convenient method of bypassing Internet filtering, for free or for a monthly fee generally between 5 and 10 US dollars, depending on the service. Free services are often either ad-supported, or limit the bandwidth and/or the maximum traffic allowed over a given period.
Popular free VPN services:
- Hotspot Shield, https://hotspotshield.com
According to a 2010 report from the Berkman Center, Hotspot Shield is overwhelmingly the most popular VPN service. For more details on how to get and use Hotspot Shield, read the "Hotspot Shield" chapter of this manual.
- UltraVPN, http://www.ultravpn.fr
- FreeVPN, http://www.thefreevpn.com
- CyberGhost, http://cyberghostvpn.com
- Air VPN, https://airvpn.org
AirVPN offers free accounts without bandwidth or traffic restrictions and without ads for activists by request. - Vpnod, http://www.vpnod.com
- VpnSteel, http://www.vpnsteel.com
- Loki Network Project, http://www.projectloki.com
- ItsHidden, http://itshidden.com
Examples of paid VPN services include Anonymizer, GhostSurf, XeroBank, HotSpotVPN, WiTopia, VPN Swiss, Steganos, Hamachi LogMeIn, Relakks, Skydur, iPig, iVPN.net, FindNot, Dold, UnblockVPN and SecureIX.
VPN standards and encryption
There are a number of different standards for setting up VPN networks, including IPSec, SSL/TLS and PPTP, that vary in terms of complexity, the level of security they provide, and which operating systems they are available for. Naturally, there are also many different implementations of each standard within software that have various other features.
- While PPTP is known to use weaker encryption than either IPSec or SSL/TLS, it may still be useful for bypassing Internet blocking, and the client software is conveniently built into most versions of Microsoft Windows.
- SSL/TLS-based VPN systems are relatively simple to configure, and provide a solid level of security.
- IPSec runs at the Internet level, responsible for packet transfer in the Internet architecture, while the others run at the Application level. This makes IPsec more flexible, as it can be used for protecting all the higher level protocols, but also difficult to set up.
Set up your own VPN service
As an alternative to paying for commercial VPN services, users with contacts in unrestricted locations may have these contacts download and install software that sets up a private VPN service. This requires a much higher level of technical knowledge, but it will be free. Also the private nature of such a setup means it is less likely to be blocked than a commercial service that has been available for a long time. One of the most widely used free and open source programs available for setting up this kind of private VPN is OpenVPN (http://openvpn.net), which can be installed on Linux, MacOS, Windows and many other operating systems.
To understand how to set up an OpenVPN system, read the "Using OpenVPN" chapter in this manual.
Advantages
A VPN provides encrypted transfer of your data, so it is one of the safest ways to bypass Internet censorship. Once configured, it is easy and transparent to use.
VPNs are best suited for technically capable users who require secure circumvention services for more than just web traffic and who access the Internet from their own computer where they can install additional software. VPNs are an excellent resource for users in censored locations who do not have trusted contacts in non-filtered locations. VPN technology is a common business application that is not likely to be blocked.
Disadvantages and Risks
Some commercial VPNs (especially the free ones) are publicly known and may be filtered. They normally cannot be used in public access locations where users cannot install software, such as Internet cafés or libraries. Use of VPNs may require a higher level of technical expertise than other circumvention methods.
A network operator can detect that a VPN is being used and determine who the VPN provider is. The network operator should not be able to view the communications sent over the VPN unless the VPN is set up incorrectly.
The VPN operator (much like a proxy operator) can see what you're doing unless you use some additional encryption for your communications, like HTTPS for Web traffic; without additional encryption, you have to trust the VPN or tunnel operator not to abuse this access.





