Introduction securing remote connection: VPN
Everybody wants to get connected to the internet, everywhere at every moment. People use whatever method is available, ranging from WiFi networks to rolling out cables on the street. It is even possible to make an internet connection using satellites or mobile networks. The urge to get connected is more important than making sure the connection is safe. Even though many people know connecting to a open wireless network is unsafe, people still act as if there is no alternative.
Although you can encrypt your web and email communication, this is unfortunately not true for all applications. There is no such encryption for MSN and nobody knows what kind of encryption Skype uses and whether it is easily to be tapped. Therefore it would be nice if you can protect your connection in a more general way. This is possible with a VPN, which stands for "Virtual Private Network".
Understanding the communication path
To get more security it's important to know what a VPN can and can't do for you. Therefore it's important to have a basic understanding of the way the internet works.
When connecting to the internet every request is going through multiple 'hops' (often called routers). At every hop a system administrator (or government institution) can spy ('sniff') on your connection. Often at least 5 to 10 hops are required before your request reaches the server. This means there are at least as many places where your information can be sniffed and leaked without your knowledge
In general (but not always!), the networks get more secure down the road. For example, if you are in China at a cafe with an unencrypted wireless connection, requesting information about Liu Xiaobo on the site http://en.wikipedia.org/wiki/Liu_Xiaobo it's very possible that this piece of information is located on a server in Amsterdam. If so, your request will travel through multiple places and each hop is vulnerable:
- the wireless network at the bar - everybody in and around the bar will be able to see your request;
- the wireless modem/router of the bar - the bar owner, or somebody with physical access to this modem/router, will be able to see your request;
- the (multiple) routers of the connection provider - in China these are controlled by the government (and probably blocked in this case), so the system administrator(s) of these networks will be able to see the request. Maybe some hundreds of system administrators have the access to 'sniff' your request.
- some routers in Europe - for example routers at the German Internet Exchange Denic in Frankfurt. Most of these systems are very well maintained and secured, but the request is still viewable by the involved system administrators;
- and finally your request will arrive at the server of Wikipedia in Amsterdam and of course the system administrator of this system will be able to see your request.
Securing the weak points
It's very important to understand that the weakest points on this path - the bar and in the country where you are - are also controlled by the people who are most interested in your requests. Therefore it's very interesting to secure this part of the path. It would be great if you can somehow change the path so it appears like your request originated in (for example) Germany instead of China. This is possible with VPN technology.
Get more security by default (with a VPN)
A VPN (Virtual Private Network) encrypts and tunnels all Internet traffic between yourself and another computer (VPN server). This computer might belong to a commercial VPN service, your organization, or a trusted contact.
Because VPN services tunnel all Internet traffic, they can be used for e-mail, instant messaging, Voice over IP (VoIP) and any other Internet service in addition to Web browsing, making everything that travels through the tunnel unreadable to anyone along the way. This makes your connection more secure by default.
If the tunnel starts at your laptop in China and ends at your VPN-provider in Germany, this can be an effective method of circumvention, since all the hops in China will only see encrypted data and have no way of knowing what data is passing through the tunnel. It has the additional effect of making all your different kinds of traffic look similar to an eavesdropper.
It is important to note that the data is only encrypted until the end of the tunnel, and then the data travels unencrypted to its final destination.
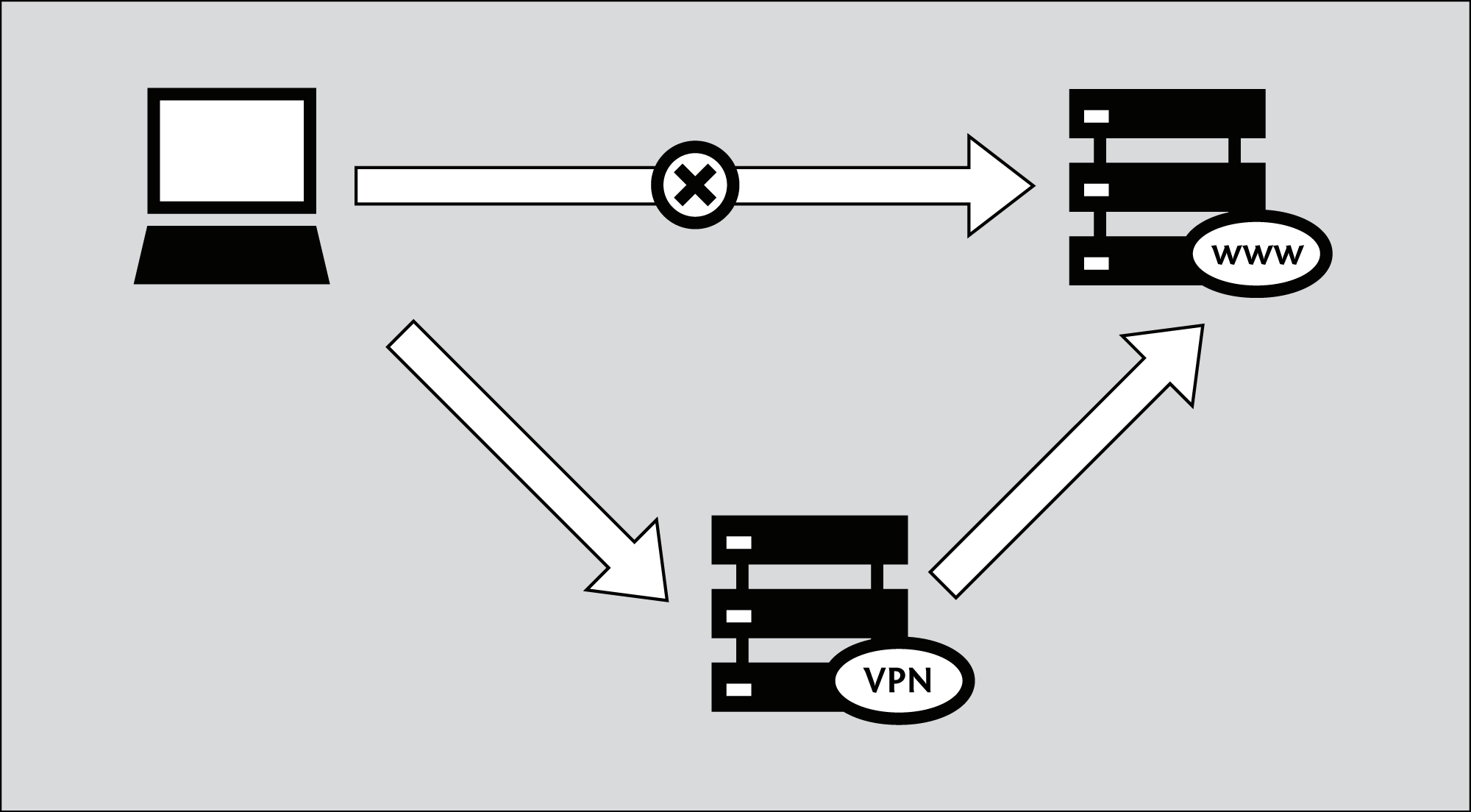
To explain the whole journey in more detail:
By using a VPN provider in Germany your request will once again be forwarded through multiple places. This time however your computer will build a VPN connection (a "tunnel") to a server in Germany, so the traffic will be as follows:
- All the hops to the VPN server in Germany will only see some unreadable encoded data - this includes the network from the bar and the Chinese firewall;
- The VPN server in Germany will receive the encrypted traffic and will decrypt it, so it can send it to some router at Denic - the request will be viewable here by the system administrator;
- Finally your request will arrive at the server of Wikipedia in Amsterdam and once again the system administrator of this system will be able to see your request.
So while not securing all parts of the data path the points where you might be most vulnerable are pretty well obscured.
Since many international companies use VPN technology to allow employees who need access to sensitive financial or other information to access the companies' computer systems from home or other remote locations over the Internet, VPN technology is less likely to be blocked than the technologies used only for circumvention purposes.
Note: The communication is only safe on one part of the path
Keep in mind that if you are communicating with a local website or person in China, your connection will be encrypted from China to Germany, but from Germany back to China (to this website or person) is unencrypted if this person is not using the proper security measures! This is important to keep in mind when communicating with local people. You may bring them and yourself in danger.





