How the Web Works
Although many people use the terms "the Internet" and "the Web" interchangeably, actually the Web refers to just one way of communicating using the Internet. When you access the Web, you do so using software called a Web browser, such as Mozilla Firefox, Google Chrome, Opera or Microsoft Internet Explorer. The protocol that the Web operates on is called the Hyper-Text Transfer Protocol or HTTP. You might also have heard of HTTPS, which is the secure version of HTTP that uses Transport Layer Security (TLS) encryption to protect your communications.
Following your information on the Internet - the journey
Let's follow the example of visiting a Web site from your home computer.
Connecting to the Internet
To connect your computer to the Internet, you may need some extra equipment, such as a modem or a router, to first connect to your ISP's network. Usually, end-user computers or home networks are connected with ISPs via one of several technologies:
- telephone modem ("dial-up"), sending Internet data over telephone lines in the form of a telephone call
- DSL, a more efficient and higher-speed way to send data over telephone lines over short distances
- cable modem (or "cable Internet"), sending Internet data over a cable television company's coaxial cable
- fiber-optic cables, particularly in densely-populated areas of developed countries
- wide-area fixed wireless links, particularly in rural areas
- data service over the mobile phone network.
Browse to the Web site
- You type in https://security.ngoinabox.org/. The computer sends the domain name "security.ngoinabox.org" to a selected DNS server, which returns a message containing the IP address for the Tactical Tech Security in a Box Web server (currently, 64.150.181.101).
- The browser then sends a request for a connection to that IP address.
- The request goes through a series of routers, each one forwarding a copy of the request to a router closer to the destination, until it reaches a router that finds the specific computer needed.
- This computer sends information back to you, allowing your browser to send the full URL and receive the data to display the page.
The message from the Web site to you travels through other devices (computers or routers). Each such device along a path can be referred to as a "hop"; the number of hops is the number of computers or routers your message comes in contact with along its way and is often between 5 and 30.

Domain names and IP addresses
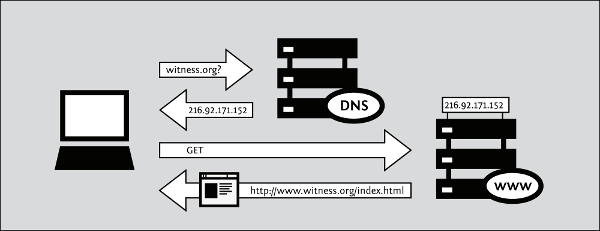
All Internet servers, such as those which host Web sites, also have IP addresses. For example, the IP address of www.witness.org is 216.92.171.152. Since remembering IP addresses is cumbersome and IP addresses might change over time, specific systems are in place to make it easier for you to reach your destination on the Internet. This system is the Domain Name System (DNS), where a set of computers are dedicated to serving your computer with the IP addresses associated with the human-memorable "names".
For example, to access the Witness Web site you would type in the www.witness.org address, also known as a domain name, instead of 216.92.171.152. Your computer then sends a message with this name to a DNS server. After the DNS server translates the domain name into an IP address, it shares that information with your computer. This system makes Web browsing and other Internet applications more human-friendly for humans, and computer-friendly for computers.
Why This Matters
Normally all of these complex processes are hidden and you don't need to understand them in order to find the information you need. However, when people or organizations attempting to limit your access to information interfere with the operation of the system, your ability to use the Internet may be restricted. In that case, understanding just what they have done to interfere with your access can become extremely relevant.
One example is DNS servers, which were described as helping provide IP addresses corresponding to requested domain names. However, in some cases, these servers can be used as censoring mechanisms by preventing the proper IP address from being returned, and effectively blocking access to the requested information from that domain.
Censorship can occur at different points in the Internet infrastructure, covering whole networks, domains or subdomains, individual protocols, or specific content identified by filtering software. The best method to avoid censorship will depend on the specific censorship technique used. Understanding these differences will help you to choose appropriate measures for you to use the Internet effectively and safely.





