Understanding basic Internet security
To understand basic internet security we should have a basic understanding of how the Internet is organised and which path our information travels. With this knowledge we can easier assess which measures we can take to protect ourselves.
The mail game
 To have a notion of how the Internet works you can compare it with the normal world wide mail network. If you want to communicate with a friend you can send her a letter and post it to the nearest mailbox; it then travels through an extensive network to (hopefully) reach the person the information is intended for. Internet is just like that, however, the message is sent in an open envelope and every postman on the way can read the message, alter its content and/or the destination without you knowing.
To have a notion of how the Internet works you can compare it with the normal world wide mail network. If you want to communicate with a friend you can send her a letter and post it to the nearest mailbox; it then travels through an extensive network to (hopefully) reach the person the information is intended for. Internet is just like that, however, the message is sent in an open envelope and every postman on the way can read the message, alter its content and/or the destination without you knowing.

To counter this, people have long used secret languages to communicate safely. In this chapter we will explain two methods of encryption. The first method explains an end-to-end encryption, encrypting the whole way from sender to receiver. The second method partly encrypts the route.
End-to-end encryption
If you encrypt your message and only the recipient can read it, it will be meaningless to all the postmen in between, and if they alter it you will notice it directly. In order to make such an encryption work, you still have to be sure to trust the recipient and be sure that you are really exchanging information with her and not with someone pretending to be her. This method is called end-to-end encryption and is the safest way of communication. You also have to be sure that no one is watching over your shoulder while you write your message. Some of the end-to-end encryption methods that we cover in this book are HTTPS for browsing and PGP for e-mailing.
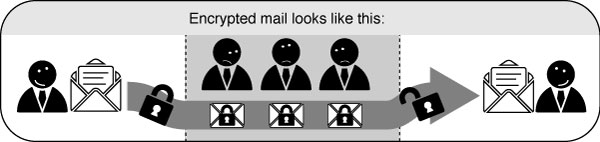
Unfortunately for end-to-end encryption to work, both you and your friend (source, co-worker) need to have the tools to use it and have to agree on the secret language used. On the internet this means the website you are visiting or the people you are e-mailing. This not always the case, still, we can considerably increase our online safety by encrypting a part of the route.
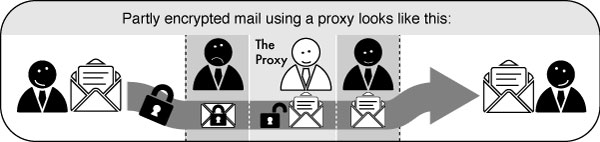
Partly encrypted mail through a proxy
To get back to the mail analogy you might be on a field trip in a repressive country and want to send a message to your friend at home. You don't trust the post offices and the postmen in this country. So before you left, you asked your local post office to act as an intermediary (the proxy) and agreed to use a secret language. Now you can just write a message to your friend in the secret language of your post office. You will send this to your post office and they will take care of the delivery of the message to your friend. In this scenario you have to trust your local post office, all the postmen after that, and of course your friend.
Visiting websites is communicating
Because in this example an analogy was drawn with mail messages, you probably thought of e-mails when reading this. While this is true, the example also counts for all other internet communications. Visiting a website is just like sending the message to your friend "please mail me your copy of the book 1984", after which she sends it to you.
Let's follow the example of visiting a website from your home computer:
- You type in http://freepressunlimited.org/.
- The request goes through a series of routers, each one forwarding a copy of the request to a router closer to the destination, until it reaches a router that finds the specific computer needed.
- This computer sends information back to you, allowing your browser to display the page.
The message that is transmitted from the website to you travels through other devices (computers or routers). The amount of devices your message comes in contact with along its way is often between 5 and 30.
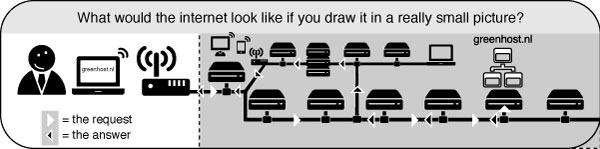
By default, information travels on the internet in an insecure way. This means that your message can be eavesdropped or tampered with on every device. If you are connecting wirelessly, people can also just "tune in" to the information send through the air.
To keep information from being compromised you have to be careful to make sure of the following:
- Can you trust the entry point (your internet connection) to the internet? If this is an insecure wireless connection anyone can eavesdrop on it, if it is a physical (cable connection) it can be eavesdropped by the operator.
- Can you trust the exit point (the site you will be visiting) of your information?
- Are you really communicating to the right destination? Or did your request end up on a server trying to appear like the server you were looking for, but really isn't.
At the end of the book there is a more in depth and technical explanation on how the net works. You can read that if you like to know more about it.





