Web Proxies
A proxy allows you to retrieve a Web site or other Internet resource even when direct access to that resource is blocked from your location. There are many different kinds of proxies, including:
- Web proxies, which only require that you know the proxy Web site's address. A Web proxy URL may look like http://www.example.com/cgi-bin/nph-proxy.cgi.
- HTTP proxies, which require that you or a piece of software modify your browser settings. HTTP proxies only work for Web content. You may get the information about a HTTP proxy in the format "proxy.example.com:3128" or "192.168.0.1:8080".
- SOCKS proxies, which also require that you or a piece of software modify your browser settings. SOCKS proxies work for many different Internet applications, including e-mail and instant messaging tools. The SOCKS proxy information looks just like HTTP proxy information.
A Web proxy is like a browser embedded inside a Web page, and typically features a small form where you can submit the URL of the Web site that you want to access. The proxy then shows you the page, without requiring that you connect to it directly.
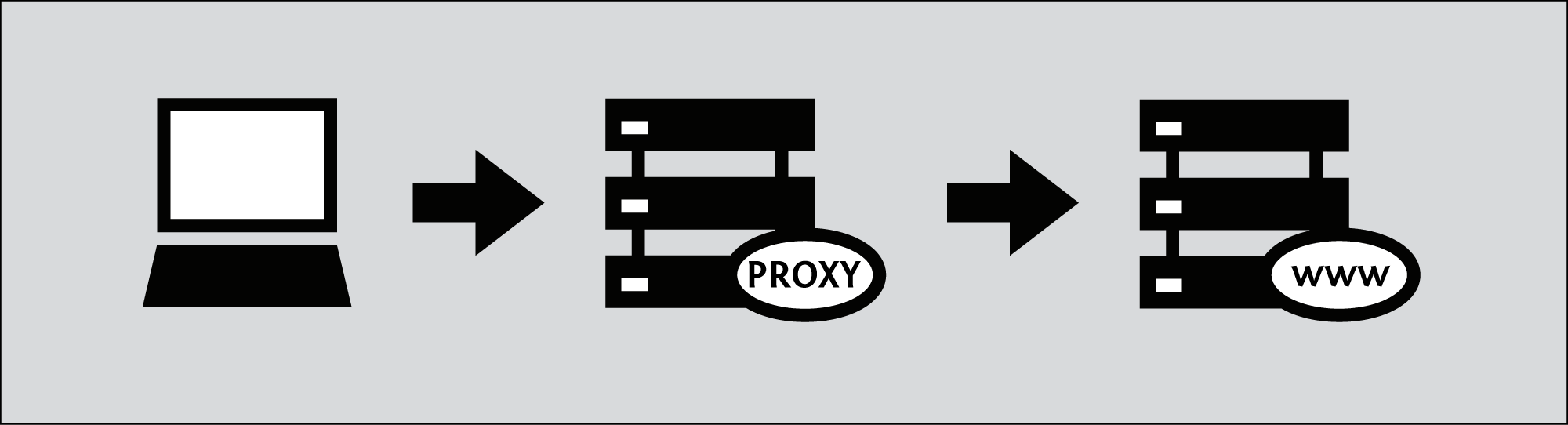
When using a Web proxy, you do not have to install software or change settings on your computer, which means that you can use a Web proxy from any computer, including those at Internet cafés. Simply enter the URL of the Web proxy into your browser, enter the destination URL you wish to visit into the Web proxy, and press Enter or click the submit button.
Once you are viewing a page through a Web proxy, you should be able to use your browser's forward and back buttons, click on links and submit forms without losing your proxied connection to the filtered site. This is because your proxy has rewritten all of the links on that page so that they now tell your browser to request the destination resources through the proxy. Given the complexity of today's Web sites, however, this can be a difficult task. As a result, you might find that some pages, links or forms "break out" of the proxied connection. Typically, when this happens, the Web proxy's URL form will disappear from your browser window.
How can I find a Web proxy?
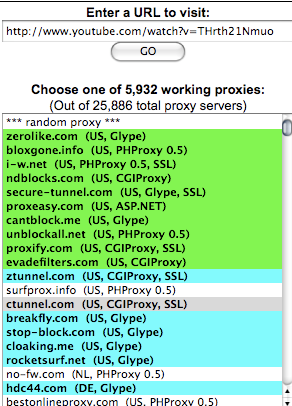
You can find Web proxy URLs at sites such as http://www.proxy.org, by signing up for a mailing list such as the one at http://www.peacefire.org/circumventor, by following a country-specific twitter feed, or simply by searching for "free Web proxy" in a search engine. Proxy.org lists thousands of free Web proxies:
Examples of Web proxy platforms include CGIProxy, PHProxy, Zelune, Glype, Psiphon, and Picidae. As mentioned above, these are not tools that you install on your own computer. They are server software that someone else must install on a computer that is connected to the Internet in a location that is not subject to filtering. All of these platforms provide the same basic functionality, but they look different and may have different strengths and weaknesses. Some are better at certain things, such as streaming videos or displaying complex Web sites accurately.
Some Web proxies are private. These are usually accessible only to a small group of users known to the individual running the proxy or to customers who pay for the service. Private Web proxies have certain advantages. Specifically, they may be:
- more likely to remain undiscovered and therefore accessible
- less congested and therefore faster
- more trustworthy, assuming they are encrypted (see below) and run by someone you know.
Access may be restricted by requiring users to log in with a username and password or simply by preventing the proxy URL from appearing in public directories such as those described above.
Web proxies are easy to use, but they have major disadvantages relative to other circumvention tools. As a result, people often use them as a temporary way to obtain and learn how to use more advanced tools, which must often be downloaded from Web sites that are themselves filtered. Similarly, access to a Web proxy can be useful when attempting to fix or replace another tool that has stopped working.
Compatibility issues with Web proxies
Web proxies only work for Web traffic, so they can not be used for other Internet services such as e-mail or instant messaging. Many are also incompatible with complex Web sites like Facebook, streaming multimedia content on sites such as YouTube, and encrypted sites that are accessed through HTTPS. This latter restriction means that many Web proxies will be unable to help you reach filtered sites that require a login, such as Web-based e-mail services. Worse yet, some Web proxies cannot themselves be accessed through HTTPS. If you use such a proxy to log in to a destination site that is normally secure, you may be putting your sensitive information, including your password, at risk.
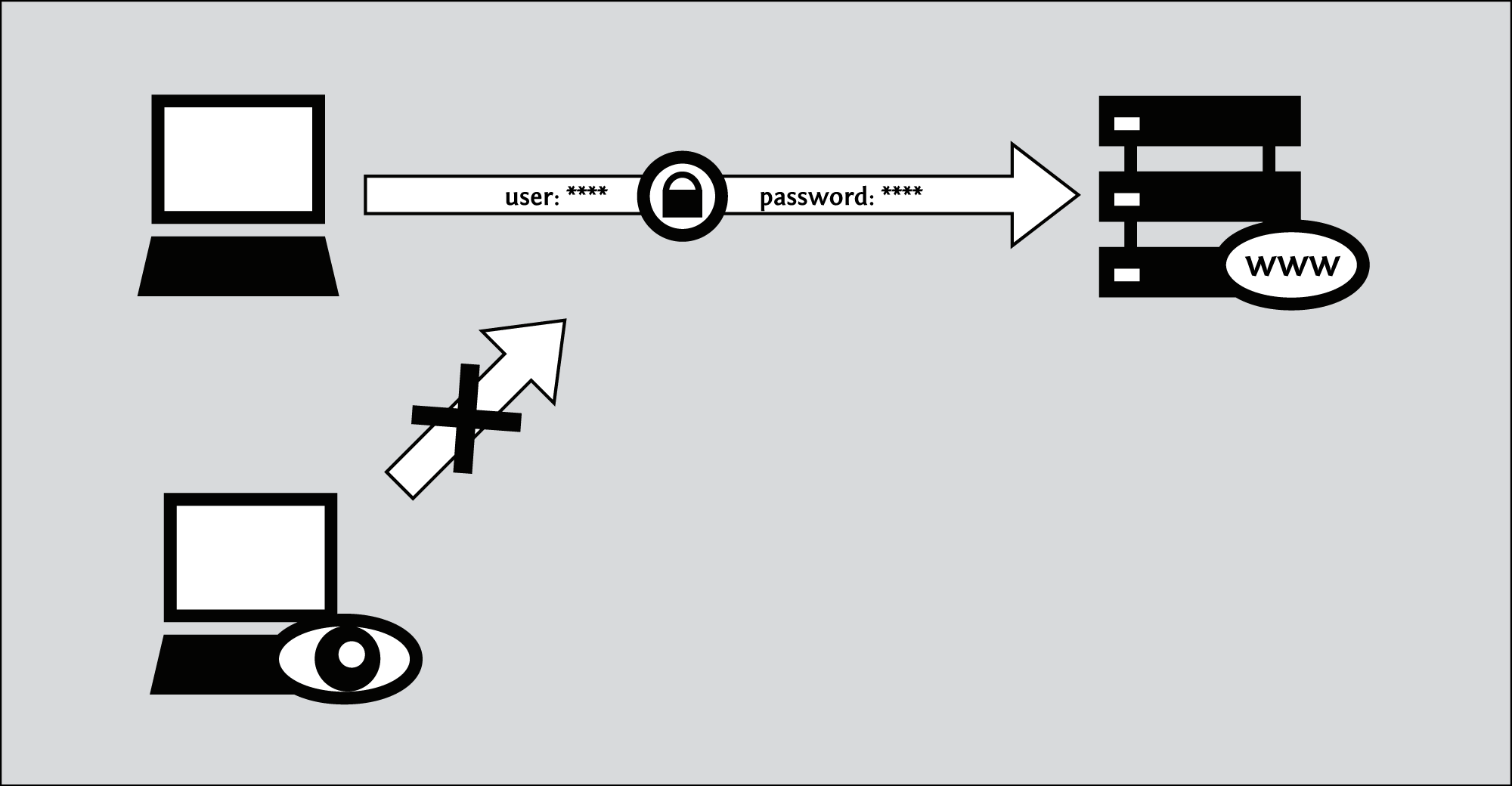

Security issues like this are discussed in more detail below.
With the notable exception of the HTTPS concerns described above, most Web proxy compatibility issues can be resolved by using the "mobile" or "basic HTML" version of the destination Web site, provided one is available. Unfortunately, relatively few sites offer this kind of simplified interface, and even fewer do so in a way that exposes all of the site's functionality. If a Web site does provide a mobile version, its URL will frequently begin with an "m" instead of "www." Examples include https://m.facebook.com, http://m.gmail.com, and https://m.youtube.com. You can sometimes find a link for the mobile or basic HTML version of a Web site among the small links toward the bottom of the site's main page.
Security risks with Web proxies
You should be aware of some of the risks associated with the use of Web proxies, particularly those operated by individuals or organizations you do not know. If you use a Web proxy simply to read a public Web site such as www.bbc.co.uk, your only real concerns are that:
- someone might learn that you are viewing a censored news source
- someone might learn which proxy you rely on to do so.
For some users, the risks above are not a major concern. However, they may become quite serious if you intend to use a Web proxy to access certain types of online resources, such as:
- sites that require you to log in with a password
- sites through which you intend to access sensitive information
- sites through which you intend to create or share content
- online commerce or Web banking sites
- sites that support HTTPS encryption themselves.
In such cases, you should avoid using insecure or untrusted Web proxies. In fact, you might want to avoid using a Web proxy altogether. While there is no guarantee that a more "advanced" tool will be more secure, the challenges that installable circumvention software must address in order to keep your traffic private are generally less complex than those faced by Web proxy software.
Obfuscation is not encryption
Some Web proxies, most notably those that lack support for HTTPS, use simple encoding schemes to circumvent poorly-configured domain name and keyword filters. One such scheme, called ROT-13, replaces each character with whatever lies 13 places ahead of it in the standard Latin alphabet. (See http://www.rot13.com to try it out for yourself.) Using ROT-13, the URL http://www.bbc.co.uk becomes uggc://jjj.oop.pb.hx, which would make it unrecognizable to a very basic keyword filter. Proxy designers have found this trick useful even in countries where keyword filtering is not present, because Web proxies often include the target URL inside the actual URL that your browser sends to the proxy every time you click on a link or submit a new address. In other words, when using a proxy, your browser might request http://www.proxy.org/get?site=http://www.bbc.co.uk instead of just http://www.bbc.co.uk, but a domain name filter written to catch the latter would catch the former just as readily. http://www.proxy.org/get?site=uggc://jjj.oop.pb.hx, on the other hand, might slip through the filter. Unfortunately, character encoding schemes are not very reliable. After all, there is nothing to prevent a censor from adding "jjj.oop.pb.hx" to the blacklist along with "www.bbc.co.uk." (Or, better yet, she could add "uggc://" to the list, which would block all use of the proxy.)
The important thing to remember about character encoding is that it does not protect your anonymity from third party observers, who can still track the list of sites that you visit. And, even if it is applied to the full text of the pages you view and content you submit (rather than just to URLs), it still can not provide confidentiality. If these things matter to you, restrict your use of Web proxies to those that support HTTPS.
Don't forget, the proxy administrator can see everything.
The advice above emphasizes the importance of HTTPS, both on the censored target site and on the proxy itself, when using a Web proxy to create or obtain sensitive information. However, it is important to note that even when you access a secure site through a secure proxy, you are still putting a great deal of faith in whoever administers your Web proxy, as that individual or organization can read all of the traffic that you send or receive. This includes any passwords that you might have to submit in order to access the destination Web site.
Even the more advanced circumvention tools, which tend to require that you install software on your computer, must rely on some kind of intermediary proxy in order to circumvent Web filters. However, all reputable tools of this kind are implemented in such a way as to protect the content of HTTPS Web traffic even from the circumvention services themselves. Unfortunately, this is not possible for Web proxies, which must rely more heavily on good old-fashioned trust. And trust is a complicated function, that depends not only on a service administrator's willingness to protect your interests, but also on her logging and record-keeping policies, her technical competency, and the legal and regulatory environment in which she operates.
Anonymity risks with Web proxies
Tools designed to circumvent filtering do not necessarily provide anonymity, even those that might include words like "anonymizer" in their names! In general, anonymity is a much more elusive security property than basic confidentiality (preventing eavesdroppers from viewing the information that you exchange with a Web site). And, as discussed above, even to ensure basic confidentiality through a Web proxy requires, at the very least, that you:
- use an HTTPS Web proxy
- connect through that proxy to an HTTPS destination Web site
- trust the proxy administrator's intentions, policies, software and technical competence
- heed any browser warnings, as discussed in the HTTPS chapter of this book.
Advertising, viruses and malware
Some of the people who set up Web proxies do it to make money. They may do this simply and openly by selling advertisements on each proxied page, as in the example below.
Or, a malicious proxy administrator might try to infect his users' computers with malware. These so-called "drive-by-downloads" can hijack your computer for spamming or other commercial or even illegal purposes.
The most important thing you can do to protect yourself against viruses and other malware is to keep all of your software – especially your operating system and your anti-virus scanner – updated. You can also block ads by using the AdBlockPlus extension (http://www.adblockplus.org) and some malicious content by using the NoScript extension (http://noscript.net). Both of these extensions are for the Firefox Web browser. You can find more information on avoiding the risks described above on the StopBadware Web site (http://www.stopbadware.org).
Cookies and scripts
There are also risks associated with the use of cookies and embedded scripts. Many Web proxies can be configured to remove cookies and scripts, but many sites (for example, social networking sites like Facebook and media streaming sites like YouTube) require them to work properly. Web sites and advertisers can use these mechanisms to track you, even when you use proxies, and to produce evidence that, for example, the person who did one thing openly is the same person who did another thing anonymously. Some cookies may be saved on your computer even after you restart it, so it might be a good idea to allow only selective use of cookies. In Firefox, for example, you can instruct the browser to accept cookies only "Until I close Firefox". (Similarly, you can instruct your browser to erase your browsing history when you close it.) Generally speaking, however, Web proxies are extremely limited in their ability to protect your identity from the Web sites that you access through them. If this is your goal, then you will have to be very careful how you configure your browser and proxy settings, and you might want to use a more advanced circumvention tool.
Helping others
If you are in a country with unrestricted Internet access and you are willing to help others get around censorship, you can install a Web proxy script on your own Web site (or even on your home computer), as discussed in the Helping Others section of this book.





