Quickstart
The Internet is censored when the people or groups controlling a network prevent Internet users from accessing particular content or services.
Internet censorship takes many forms. For example, governments may block regular e-mail services in order to compel citizens to use government e-mail that can be easily monitored, filtered, or shut down. Parents can control the content their minor children access. A university may prevent students from accessing Facebook from the library. An Internet caf owner can block peer-to-peer file sharing. Authoritarian governments may censor reports on human rights abuses or the last stolen election. People have widely varying views about the legitimacy or illegitimacy of these forms.
Circumvention
Circumvention is the act of bypassing Internet censorship. There are many ways to do this, but nearly all circumvention tools work in approximately the same manner. They instruct your Web browser to take a detour through an intermediary computer, called a proxy, that:
- is located somewhere that is not subject to Internet censorship
- has not been blocked from your location
- knows how to fetch and return content for users like you.
Security and anonymity
Keep in mind that no tool is a perfect solution for your situation. Different tools offer varying degrees of security, but technology cannot eliminate the physical risks you take by opposing people in power. This book contains several chapters explaining how the Internet works which is important for understanding how to be safer while circumventing censorship.
There are many variations
Some tools only work with your Web browser, while others might be applied to several programs at once. These programs might need to be configured to send Internet traffic through a proxy. With a little extra patience, you can do all of this without installing any software on your computer. Note that tools that fetch Web pages for you may not display the site correctly.
Some tools use more than one intermediary computer in order to hide the fact that you are visiting blocked services. This also hides your activities from the tool provider, which can be important for anonymity. A tool may have a clever way of learning about alternative proxies it may connect to in case the one you are using gets censored itself. Ideally, the traffic created by all of this requesting, fetching and sending is encrypted in order to protect it from prying eyes.
But choosing the right tool for your particular situation is almost certainly not the most important decision you will make when it comes to accessing or producing content in the face of Internet censorship. Though it is difficult to provide concrete advice on such things, it is crucial to spend your time thinking about context, such as:
- how, when, and where you intend to use these tools
- who might want to prevent you from doing the things the tools allow you to do
- how strongly those organizations and individuals oppose this usage
- what resources they have at their disposal to help them achieve their desired outcome, up to and including violence.
Access most blocked Web sites without extra software
The most basic type of circumvention tool is a Web proxy. While there are many reasons why it might not be the optimal solution for you, for very basic circumvention purposes it is often a good place to start. Assuming it has not yet been blocked from your location, visit the following URL: http://sesaweenglishforum.net
Accept the Terms of Use, and enter the URL of the blocked site you wish to visit into the blue URL bar:

Press Enter or click GO, and if it successfully navigates to the requested website then it is working. If the link above does not work, you will have to find an alternative circumvention method. The Web proxy and Psiphon chapters of this book offer a little advice about finding a Web proxy and a lot of advice about deciding whether or not you should be willing to use it once you do.
If you need access to the full feature set of a particularly complex Web site such as Facebook you might want to use a simple, installable tool like Ultrasurf instead of a Web proxy. If you desire or require a solution that has been through rigorous security testing and that can help you remain anonymous without requiring that you know who actually administers the service itself, you should use Tor. If you need access to filtered Internet resources other than just Web sites, such as blocked instant messaging platforms or filtered email servers (the kind used by programs like Mozilla Thunderbird or Microsoft Outlook), you might try HotSpot Shield or some other OpenVPN service. All of these tools, which have their own chapter later in the book, are briefly described below.
Access all blocked Web sites and platforms
Ultrasurf is a free proxy tool for the Windows operating system which can be downloaded at http://www.ultrareach.com/, http://www.ultrareach.net/ or http://www.wujie.net/. The downloaded zip file has to be extracted with a right click and selecting "Extract All...". The resulting .exe file can be started directly (even from a USB flash drive in an Internet caf) without installation.
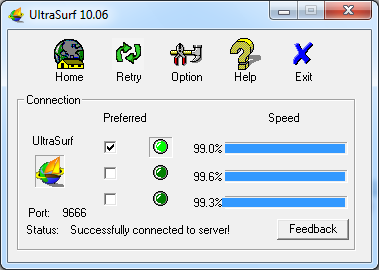
Ultrasurf connects automatically and will launch a new instance of the Internet Explorer Web browser which you can use to open blocked Web sites.
Bypass the filters and stay anonymous on the Web
Tor is a sophisticated network of proxy servers. It is free open source software developed primarily to allow anonymous Web browsing, but it is also a great censorship circumvention tool. The Tor Browser Bundle for Windows, Mac OS X or GNU/Linux can be downloaded from https://www.torproject.org/download/download.html.en. If the torproject.org Web site is blocked for you, you may find other download locations by typing "tor mirror" in your favorite Web search engine or by sending an email to gettor@torproject.org with "help" in the message body.
When you click on the downloaded file, it will extract itself to the location you choose. This may also be a USB flash drive which can be used in an Internet caf. You can then launch Tor by clicking "Start Tor Browser" (make sure you close any Tor or Firefox instances that are already running). After a few seconds, Tor automatically launches a special version of the Firefox Web browser with a test Web site. If you see the green message "Congratulations. Your browser is configured to use Tor." you can then use that window to open blocked Web sites.
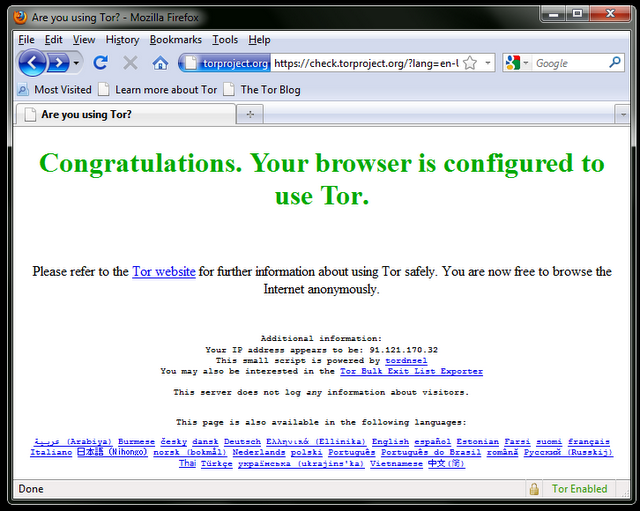
Channel all your Internet traffic through a secure tunnel
If you want to access Internet services other than the Web, such as e-mail through an e-mail client like Outlook or Thunderbird, one easy and secure way is to use a virtual private network (VPN). A VPN will encrypt and tunnel all Internet traffic between yourself and another computer, so not only will it make all your various kinds of traffic appear similar to an eavesdropper, but the encryption will make it unreadable to anyone along the way. While connecting with the VPN, your ISP will not see your content, but will be able to see that you are connecting to the VPN. Since many international companies use VPN technology to securely connect their remote offices, VPN technology is unlikely to be blocked as a whole.
Hotspot Shield
An easy way to get started with VPNs is to use Hotspot Shield. Hotspot Shield is a free (but commercial) VPN solution available for the Microsoft Windows and Mac OS X operating systems.
To install Hotspot Shield you must download the software from https://www.hotspotshield.com. The file size is about 6MB, so on a slow dial-up connection the download might take 25 minutes or more. To install, double-click the downloaded file and follow the steps presented by the installation wizard.
Once the installation is complete, start Hotspot Shield from the "Hotspot Shield Launch" icon on your desktop or via "Programs > Hotspot Shield". A browser window will open with a status page showing different stages of the connection attempt such as "Authenticating" and "Assigning IP address". Once connected, Hotspot Shield will redirect you to a welcome page. Click on "start" to begin surfing.
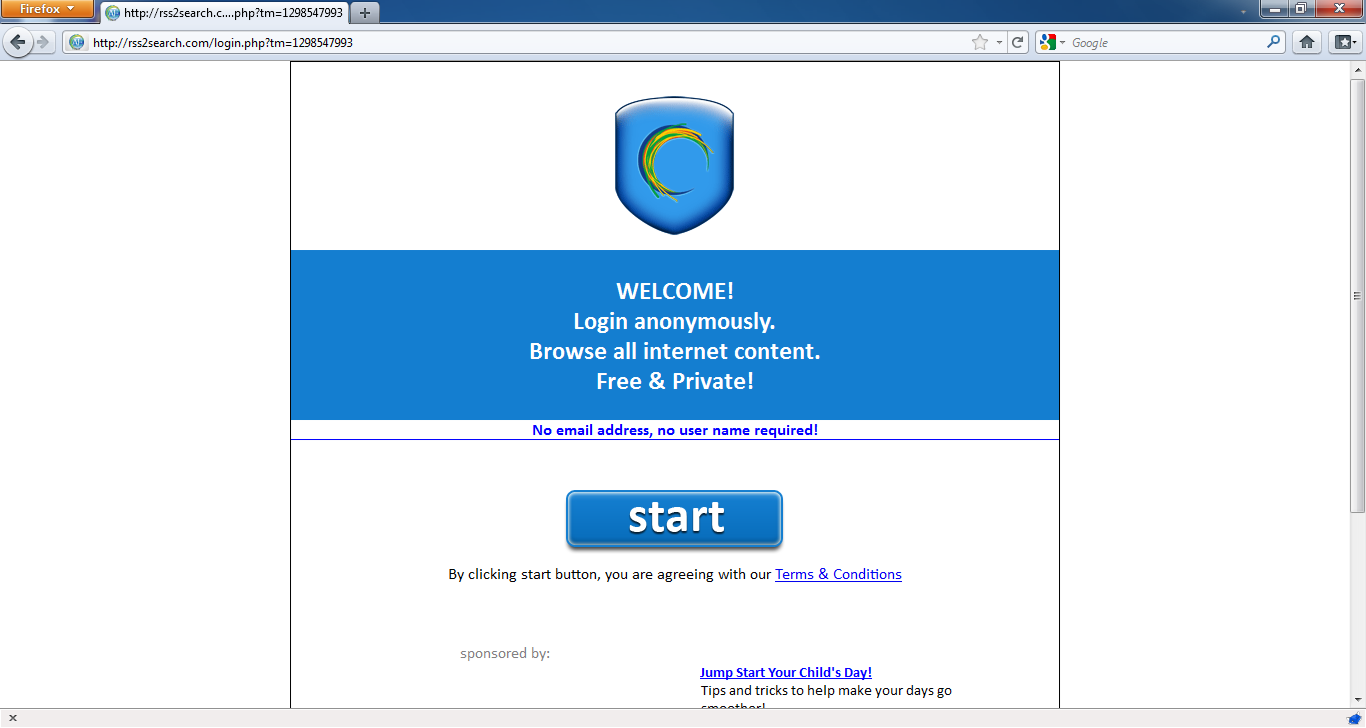
To stop Hotspot Shield, right click on the traybar icon and select "Disconnect/OFF".





