Researching and Documenting Censorship
In many countries, it is no secret that government censorship of the Internet exists. The scope and methods of censorship have been documented for example in the books Access Denied: The Practice and Policy of Global Internet Filtering and Access Controlled: The Shaping of Power, Rights, and Rule in Cyberspace, both edited by Ronald Delbert, John Palfrey, Rafal Rohozinski, and Jonathan Zittrain (http://opennet.net/accessdenied and http://www.access-controlled.net).
When a popular site is widely blocked, that fact tends to become widely known within the country. However, some governments (including some rather active censors) officially deny the existence of censorship or try to disguise it as random technical errors. If you're subject to censorship, you can use your situation to help others (including the international academic and activist community that studies censorship) understand it and potentially publicize it.
Of course, you need to be cautious about this; governments that deny their network censorship practice may not appreciate your participation in efforts to expose them.
Research censorship knowledge databases
Some censorship knowledge databases have been made public in the last couple of years. Some of them are crowd-sourced but they are all validated by field experts. They are being constantly updated to keep information and blocked sites lists as accurate as possible. Some databases are available at the following URLs:
- Herdict Web: https://www.herdict.org
-
Alkasir Map: https://www.alkasir.com/map
On a more macro-geographic level, OpenNet Initiative and Reporters without Borders release a "State of Internet" for every country on a regular basis. You can access them online:
- OpenNet Initiative research report: http://opennet.net/research
- Reporters Without Borders Internet Enemies: http://www.rsf.org/ennemis.html
Reporting blocked sites using Herdict
Herdict (https://www.herdict.org) is a Web site which aggregates reports of inaccessible sites. It's run by researchers at the Berkman Center For Internet and Society at Harvard University in the United States who study how the Internet is being censored.
The data in Herdict isn't perfect – for example, many users can't distinguish a site that is not available because of a technical glitch or because they mistyped the address from actual censorship – but the data is collected from all over the world and is constantly updated.
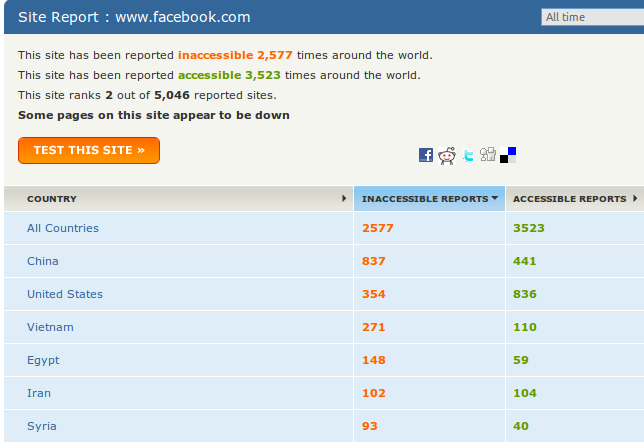
Above is an overview of the Facebook report.
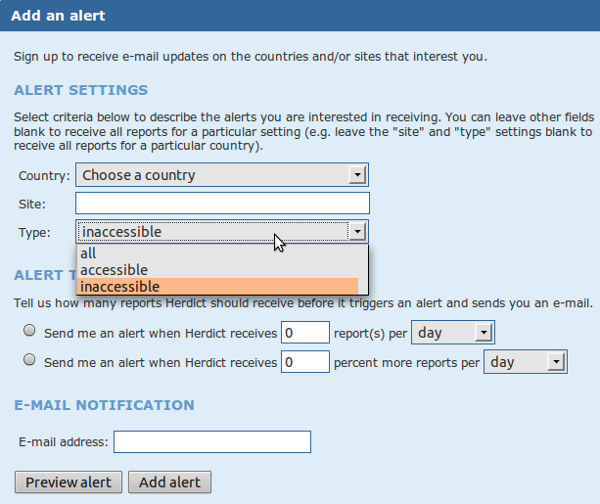
You can help these researchers by submitting your own reports to Herdict through their web site. It is free, easy to use and you don't even have to register. You can also register to get updates on future block notifications about a website.
Herdict also offers add-ons for the Firefox and Internet Explorer Web browsers to make it easier to report whether particular Web sites are blocked or not as you browse the web.
Reporting blocked sites using Alkasir
Alkasir is a censorship circumvention tool with a build in research part which allows its users to report a blocked Web site with a simple click on the "Report Blocked URLs" button. Alkasir maintains a relevant list of blocked sites per country and may automatically check other related URLs for availability. By using the report feature you can easily contribute to this research.
You can find more details about how to use the tool in the chapter "Using Alkasir".
Enabling remote access for others
You can also help censorship research by giving researchers remote access to your computer so that they can use it to carry out their own tests. You should only do this if you trust the researchers in question with the kind of access you're offering them, since they may get full control over your computer and everything they do on your machine will look like your own actions to your ISP or government.
For GNU/Linux operating systems a shell account is the best option; you can find help in setting this up at http://ubuntuforums.org and other sites.
For Windows operating systems the build-in remote desktop feature should be used. You can find instructions for this at http://www.howtogeek.com/howto/windows-vista/turn-on-remote-desktop-in-windows-vista. You may also have to change port forwarding settings on the router box you use to connect to the Internet; this is explained on http://portforward.com.
Another solution for remote access is the free tool TeamViewer (http://www.teamviewer.com) which is available for all operating systems.
Comparing notes
The basic technique for documenting network censorship is to try to access a huge number of network resources, such as a long list of URLs, from various places on the Internet and then compare the results. Did some of the URLs fail to load in one place but not in another? Are these differences ongoing and systematic? If you have a reliable circumvention technology such as a VPN, you can do some of these experiments by yourself, by comparing how the net looks with and without circumvention. For example, in the United States, this was the method used to document how ISPs were disrupting the use of peer-to-peer filesharing software.
These comparisons can be done with automated software or by hand.
Packet sniffing
If you become familiar with the technical details of how Internet protocols work, a packet sniffer like Wireshark (http://www.wireshark.com/) will let you record the actual network packets that your computer transmits and receives.





